Cosmos DB - Defender for Cloud
For our cloud security product ARGOS we use Azure Cosmos DB as our backend database.
Of course, I made sure we had all the common security practices applied. For example, we use managed identities wherever possible to communicate with Cosmos DB, instead of using keys, which have a tendency to leak via code commits for example. We ensure that our Cosmos DB Account is also not accessible by everyone on the internet, using Firewall rules and virtual network integrations.
All of this helps with good security posture and helps to protect from most of the things “we know” about.
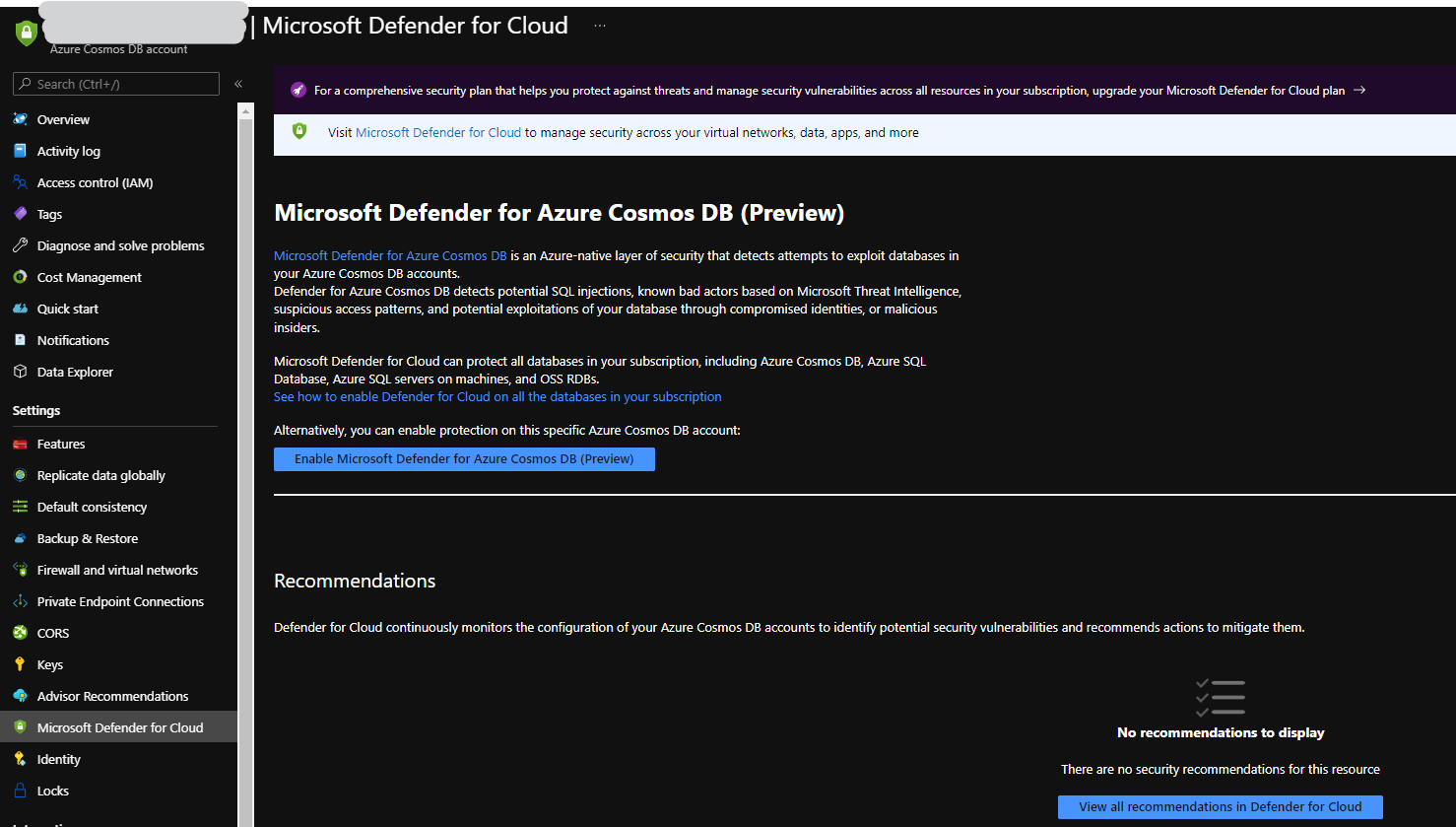
Defender for Cloud - Cosmos DB
What about the threats we do not know about though? We already use Defender for Cloud (formerly known as Security Center) quite heavily from a Threat Protection point of view, and now this is also available (as preview) for our Cosmos DB Accounts.
For now, this is only available if you are using the SQL API for Cosmos DB. See more on the official docs. The threat types that our databases and our customer data is now protected against are:
- Potential SQL injection attacks:
- Due to the structure and capabilities of Azure Cosmos DB queries, many known SQL injection attacks can’t work in Azure Cosmos DB. However, there are some variations of SQL injections that can succeed and may result in exfiltrating data from your Azure Cosmos DB accounts. Defender for Azure Cosmos DB detects both successful and failed attempts, and helps you harden your environment to prevent these threats.
- Anomalous database access patterns:
- For example, access from a TOR exit node, known suspicious IP addresses, unusual applications, and unusual locations.
- Suspicious database activity:
- For example, suspicious key-listing patterns that resemble known malicious lateral movement techniques and suspicious data extraction patterns.
If any of these events fire we will receive an alert right away and we can quickly investigate the issue.
As Microsoft runs their detections off the service’s telemetry and not “in the middle” of transactions there is no performance impact and no change to any code required.
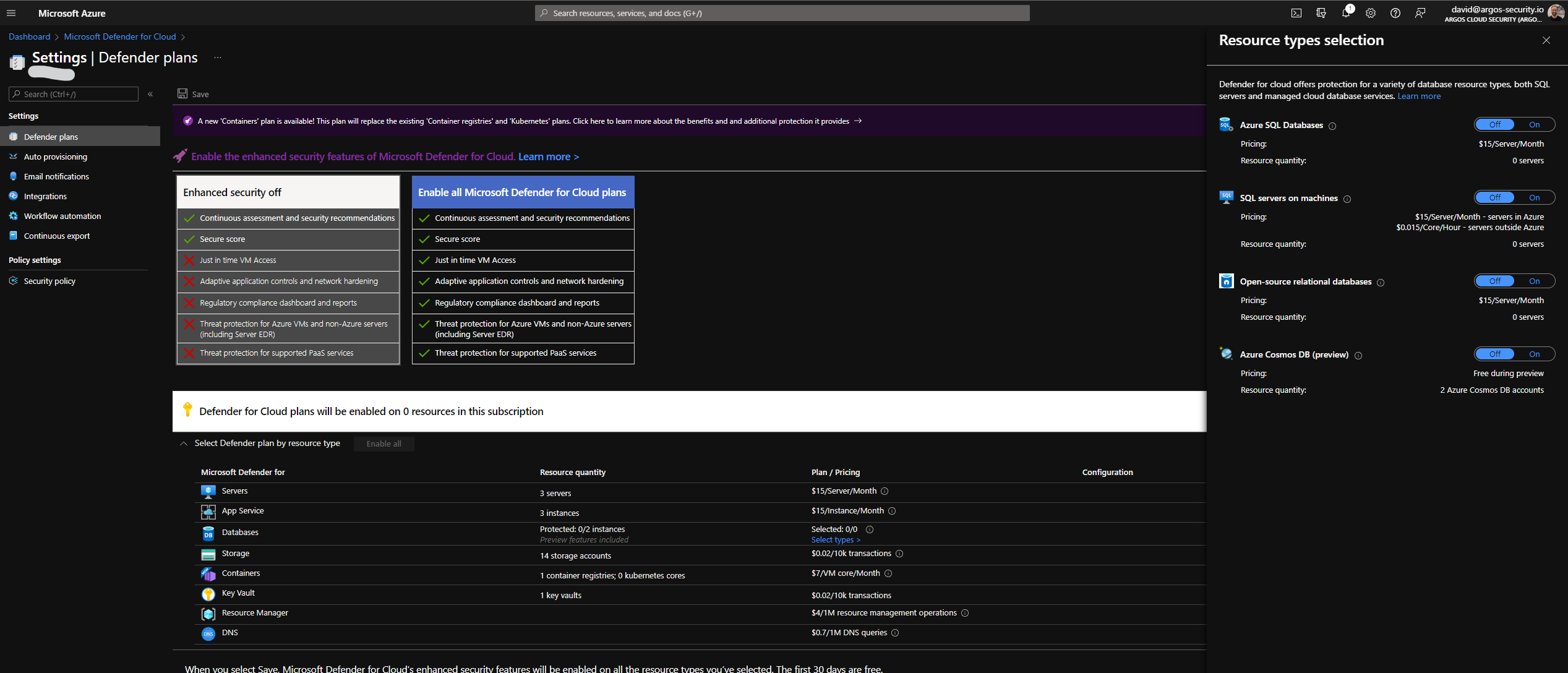
Enable Defender for Cloud by Default
You can also enable Defender for Cosmos DB by default at the Subscription level. Go to Defender Settings and enable Defender for all Cosmos DB Accounts.
I hope you’ll have a much better sleep now that your databases are protected by Defender for Cloud.